Authentication
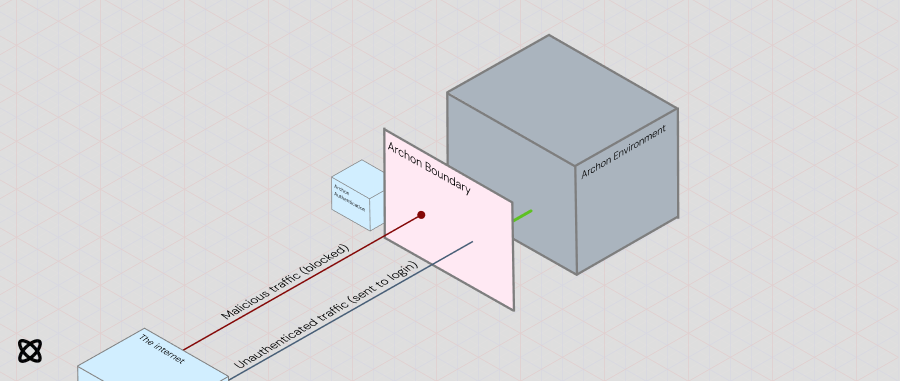
To guarantee compliance, the Archon authentication layer checks the credentials of incoming traffic before it ever enters the Archon Environment (See key terms). When in production, it also blocks incoming traffic it suspects to be malicious.
All traffic that has entered the environment is guaranteed to be authenticated before reaching your application.
When an unauthenticated user attempts to access the environment, they will be forwarded to a public-facing login page. After successfully logging in, users will be provided a session cookie that uniquely identifies them.
Users
Users have the following properties:
- uuid: The unique identifier for this user
- username: The unique username for this user
- userSource: The origin of this user
archon: Reserved for Archon administrative activities that may occur when your application is running in productionyour_org: A user from your company. Your devs and administrators should have this sourceclient: A user from an organization you sell to. This could be a government entity, contractor, etc.service: An automated account that performs actions. These accounts can only authenticate from within your environment, and cannot sign in via a login prompt.
Sessions
Traffic beyond the boundary is always associated with a session. Sessions contain the following information:
- A
user: The person (or application) performing actions against your application - A
role: The set of actions this person can take- For more information on roles, see Role
HTTP requests associated with a session will have an X-Session-ID header that can be used to get information about a session from the Engine. SDKs also provide utility methods to gather session information from request objects.
The login process
The login process looks as follows:
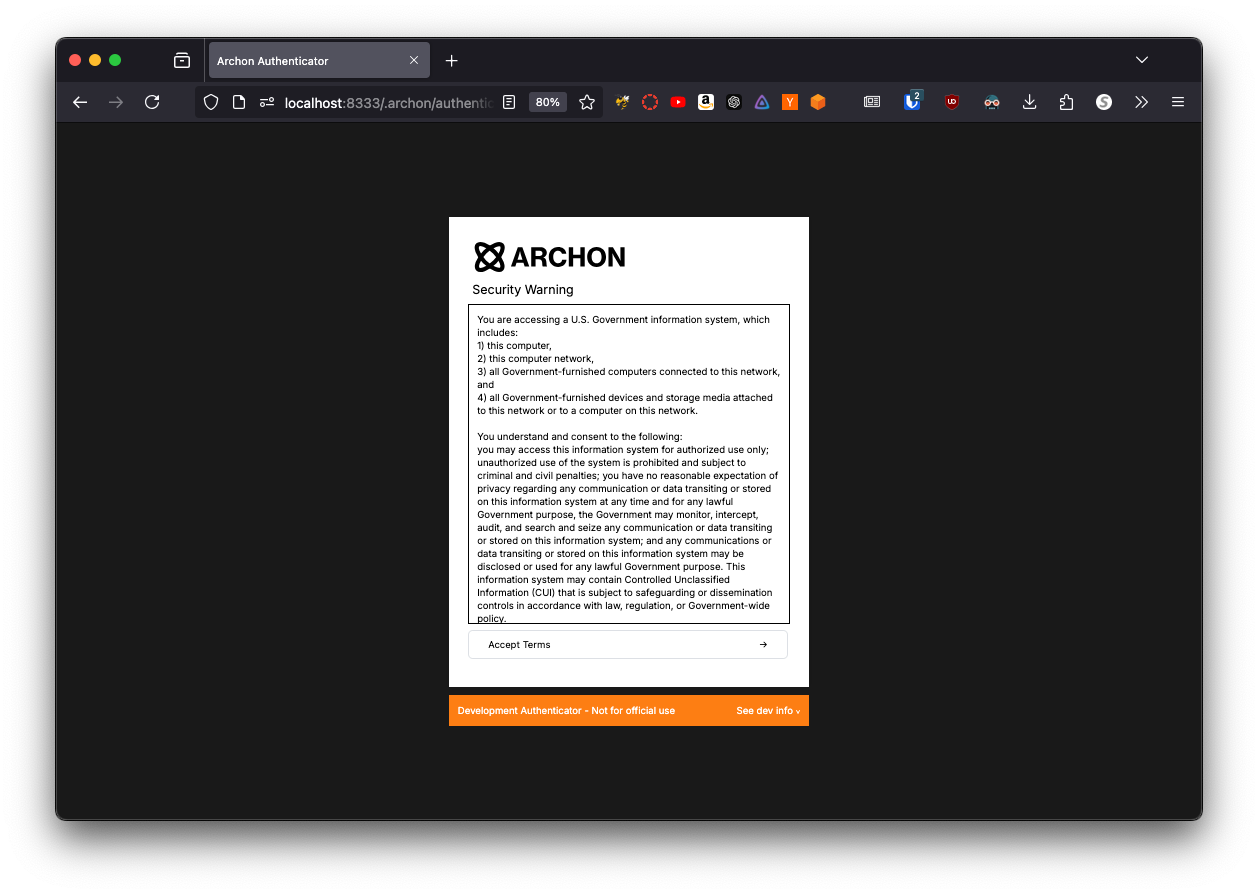
- Users are presented with a security warning for accessing controlled government information
- Users then select the authentication method they would like to use
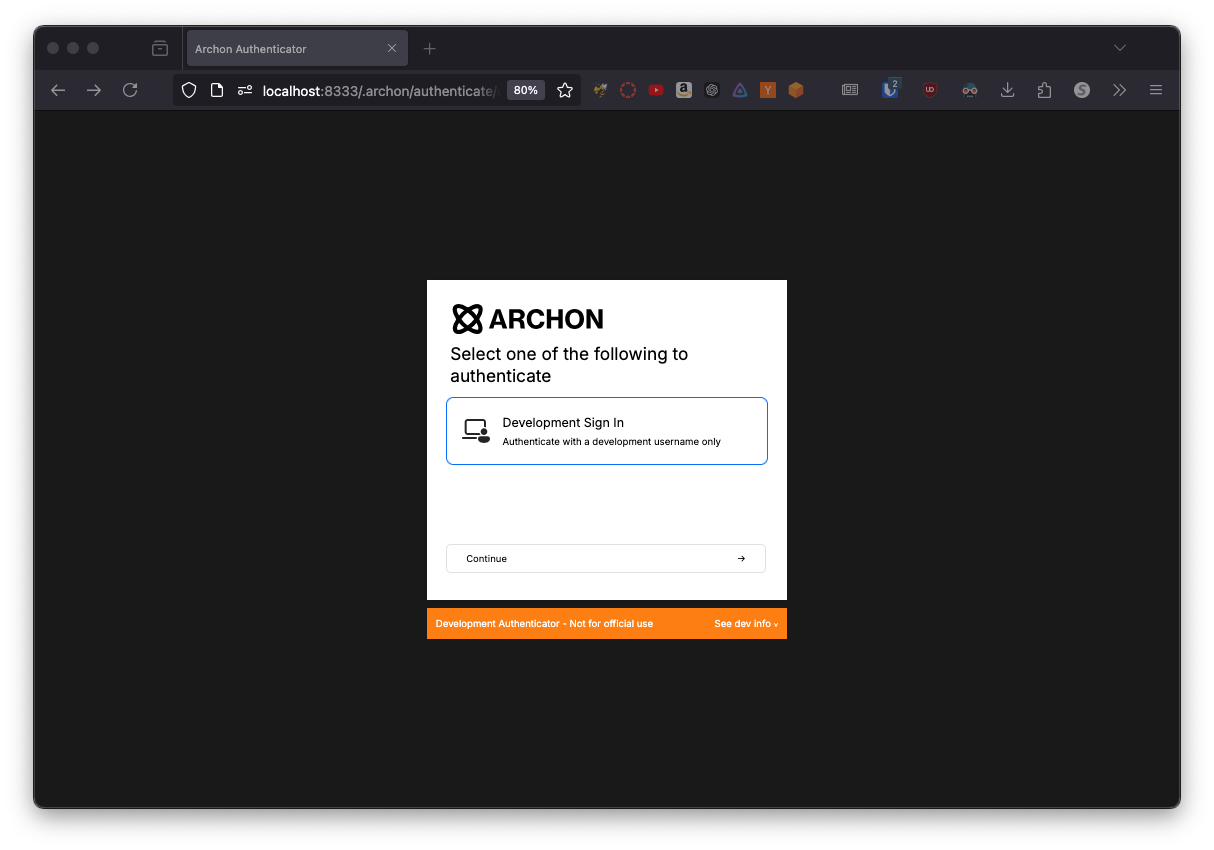
This section only applies to development mode
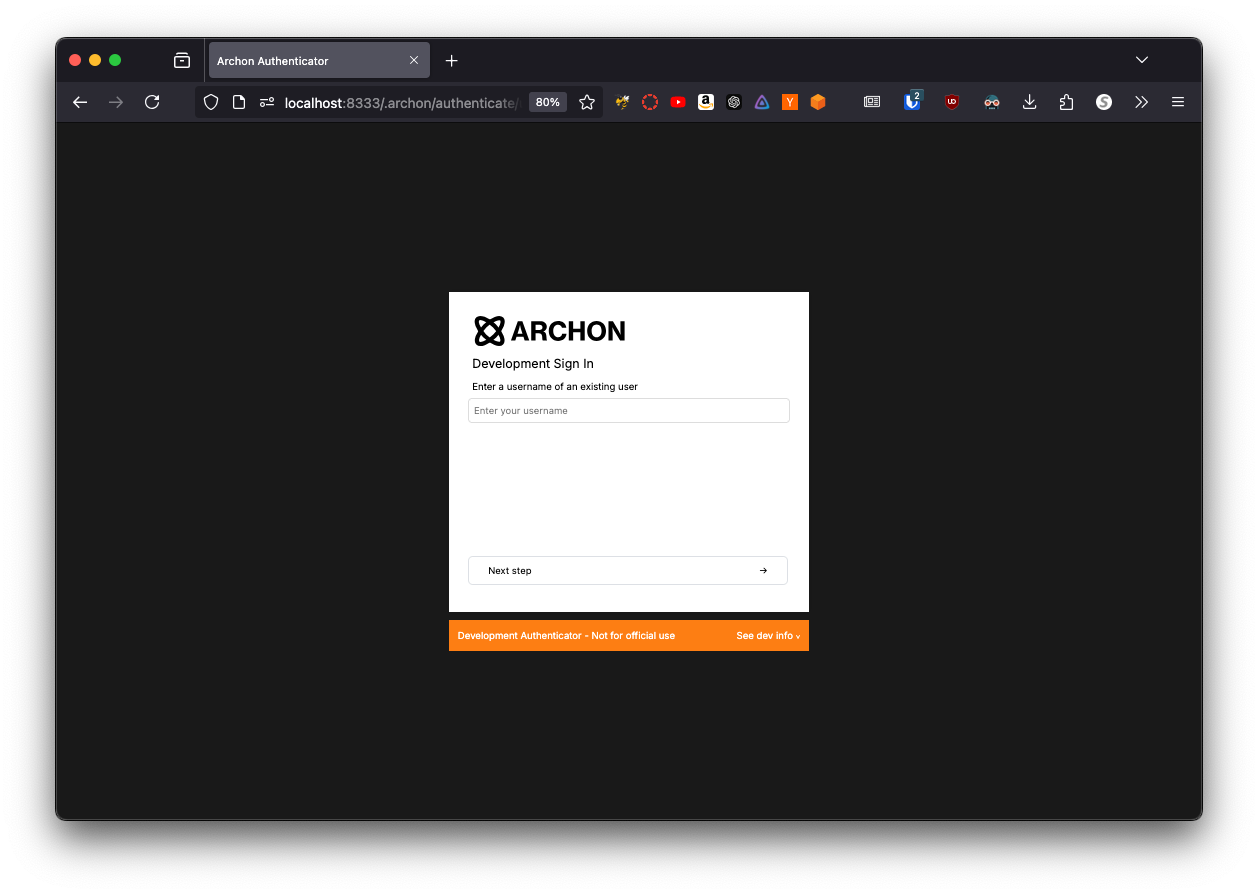
- When in development mode, users can sign in with just a username of a non-service account
- Users will also be routed through an already approved 2FA screen.
- Users now have access to your application!